Methodology
No Marketing. Proven results.
Our promise: budget and management support for Active Directory security.
Step 1: Understand the stakeholders
There are two main stakeholders in the Active Directory landscape: the IT Management which is holding budget decision and the IT Operations which ensure that the Active Directory stays up and running.

IT Management: Their needs
Assess the Current security level
Avoid the presence of Critical Risks
Get advice to prioritize the items in the Action plan
What is the cost of doing that or that? Management has to arbitrate with many topics and if they agree that everything should be done, there is a limit in the budget they can spend. And they have to share it with so many subjects.

IT Operations: Their needs
Detect critical security issue
Overview of the technical situation
Guidance & Advices to fix issues
Step 2: Prepare the battle plan
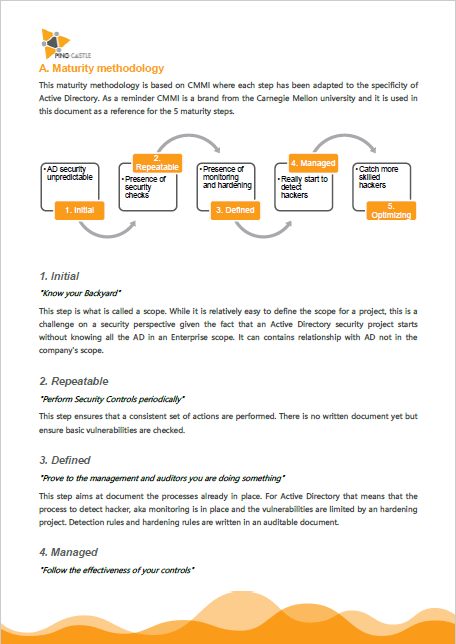
Step 3: “Know your Backyard”
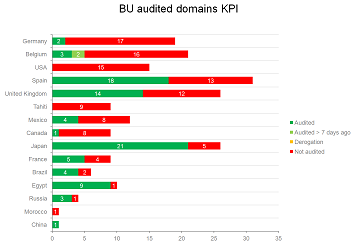
The goal is to reach the Level 1 of the maturity model by defining the “scope”. The scope can be considered as the set of domains to put under control and in order to define it, there need to be a discovery phase. Here are the 3 key areas to question:
Domain coverage
Do you actually know how many domains you have in your Active Directory?
Ownership
Are you sure that all your domains are actually monitored by someone?
External trusts
Are you aware that your domains are exposed on the Internet without protection?
The goal is to prevent forgotten domains or trusts belonging to external companies over which you have no control.
Key decisions to take:
- Deploy the tool on 100% of the domains at least once
- Assign all domains found to an owner
- If it is not possible to get ownership, remove the trust to these domains
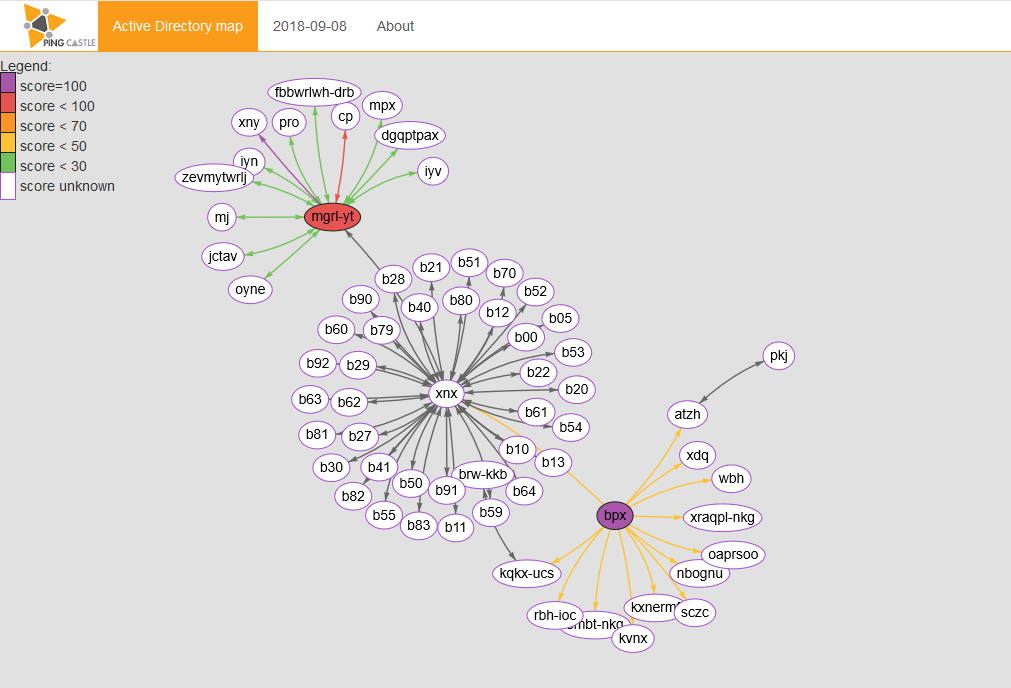
Active Directory map
Learn how to build a map of your domains with PingCastle
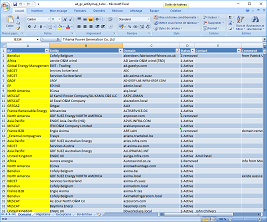
The two main activities on this step are the map and the reference file. While the reference file is just an Excel file based on a template, the map can be built quickly with the carto mode or by aggregating many health check reports at once.
Ownership assignments
Step 4: “Perform Security Controls periodically”
Internal trusts
Do you realise that badly implemented trusts provoke a major risk of cross-contamination?
Risk score control
Are you aware of all the possible security issues that may be in your Active Directory?
Establish governance to secure budget allocation
Key decisions to take:
- Get health check report every week
- Request the implementation SID Filtering on 100% of the trusts except official migrations
- Set an objective on risk score reduction (30 for example)
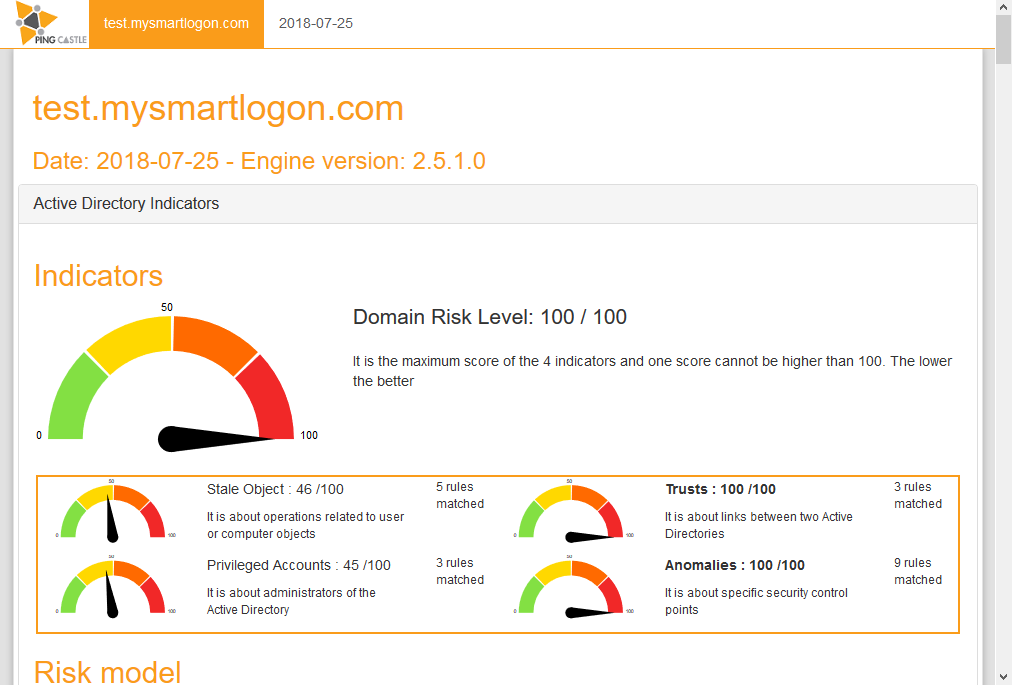
Health Check
Check out main vulnerabilities and how your score evolves with time.
The two main activities on this step are to collect the vulnerabilities with the health check mode and report your progress to the management. The health check mode is built in minutes. When multiples reports are collected, you can use the configuration file generated at the step above to generate automatically the dashboard.