Cartography
How to produce Active Directory mapsA map is the representation of the Active Directories linked by “trusts”. It can be less or more accurate depending on the freshness of the information and the depth of the trust links. Indeed, when starting this process, there is no much information available and PingCastle uses a set of tricks to extend it as much as possible.
Prerequisites
Existing reports
This is the reports produced in the past by PingCastle
AD connectivity
Access to the Active Directory via a local account or an account from a trusted domain
When having existing health check reports
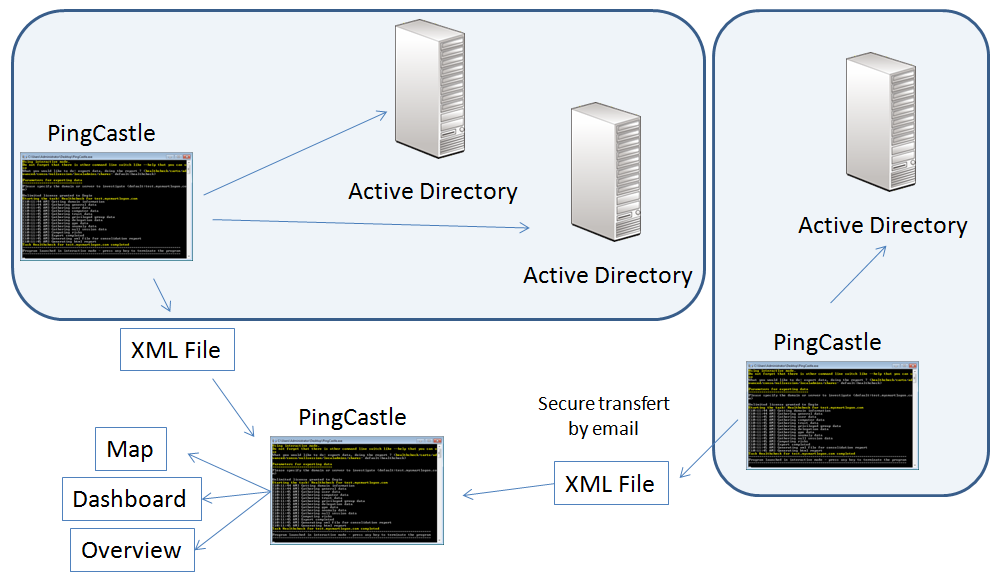
The map can be generated in the interactive mode by choosing “conso”. This mode performs the consolidation report and build the maps.
It can be run using the command:
PingCastle.exe --hc-conso
When no health check report is available
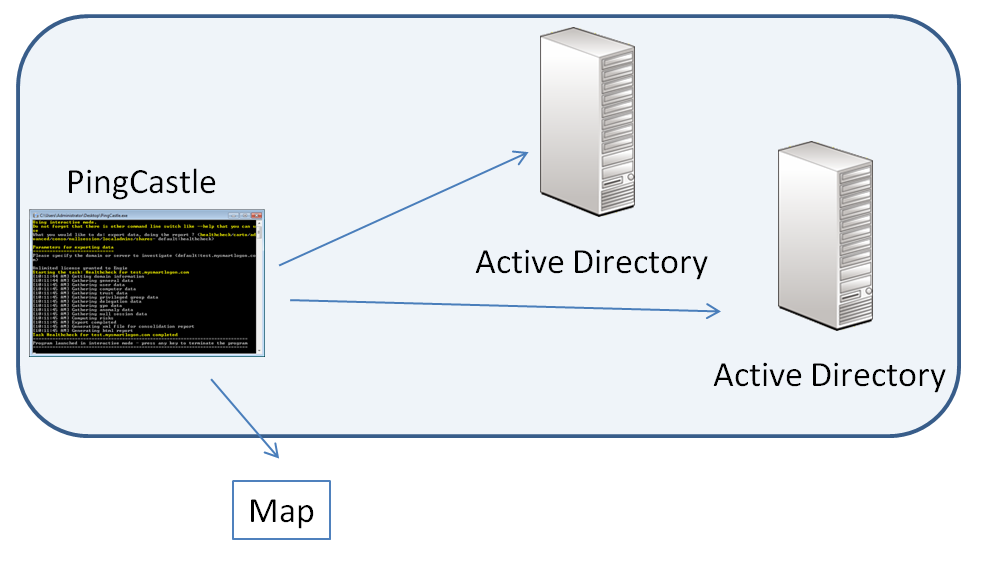
The map can be generated in the interactive mode by choosing “carto”. This mode performs only the part needed for building the map in the health check process to all the available domains. This mode cannot combine existing health check reports.
It can be run using the command:
PingCastle.exe --carto
Description
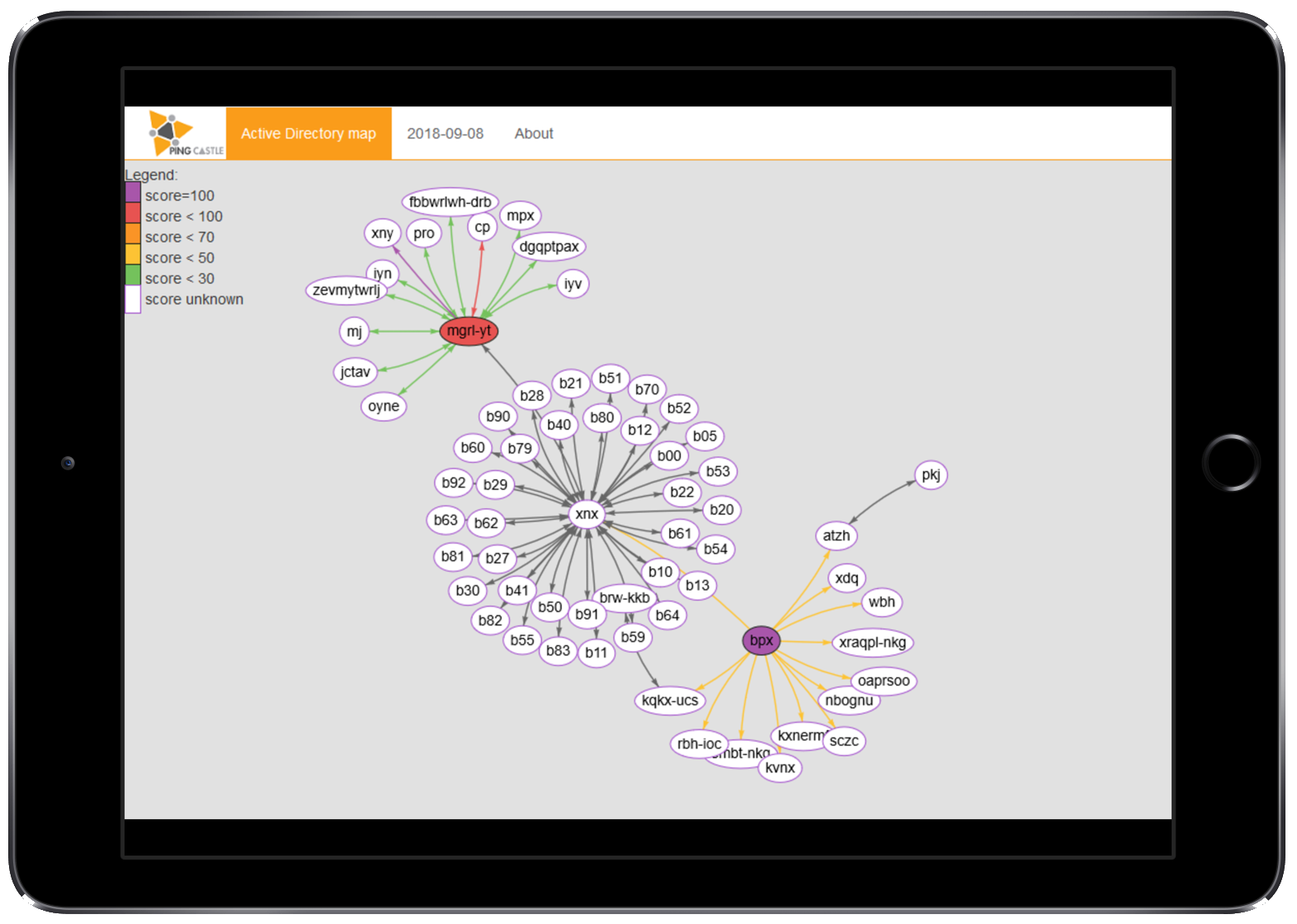
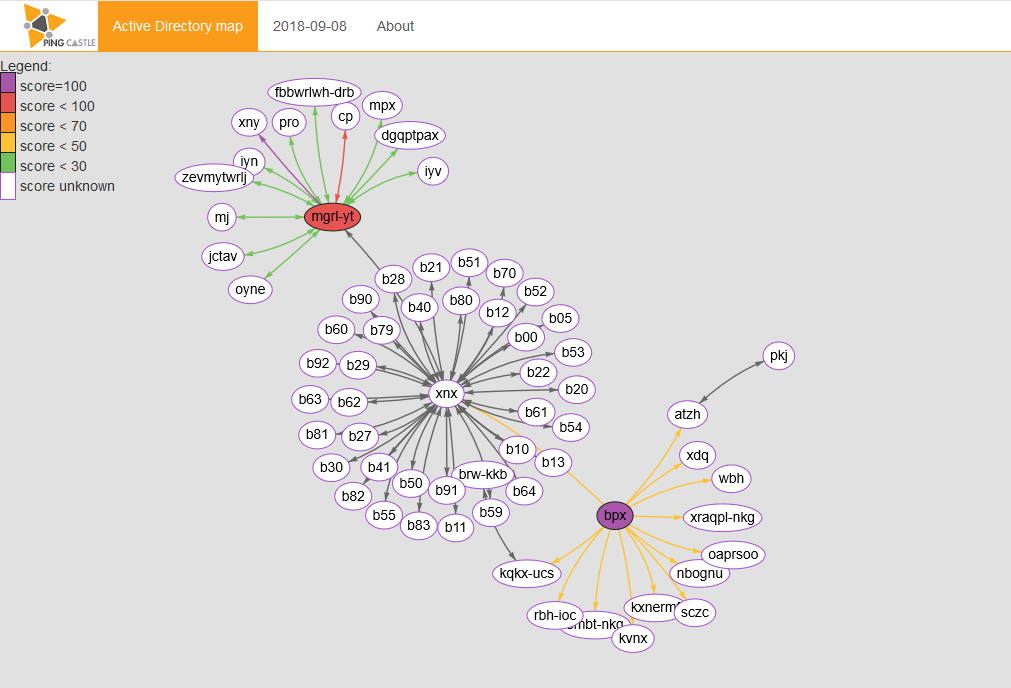
There are two kinds of map. The first one is the most complete but can be difficult to read. To avoid this difficulty, a simplified most exists where a domain is connected to others only using a single trust. It builds a hierarchy.
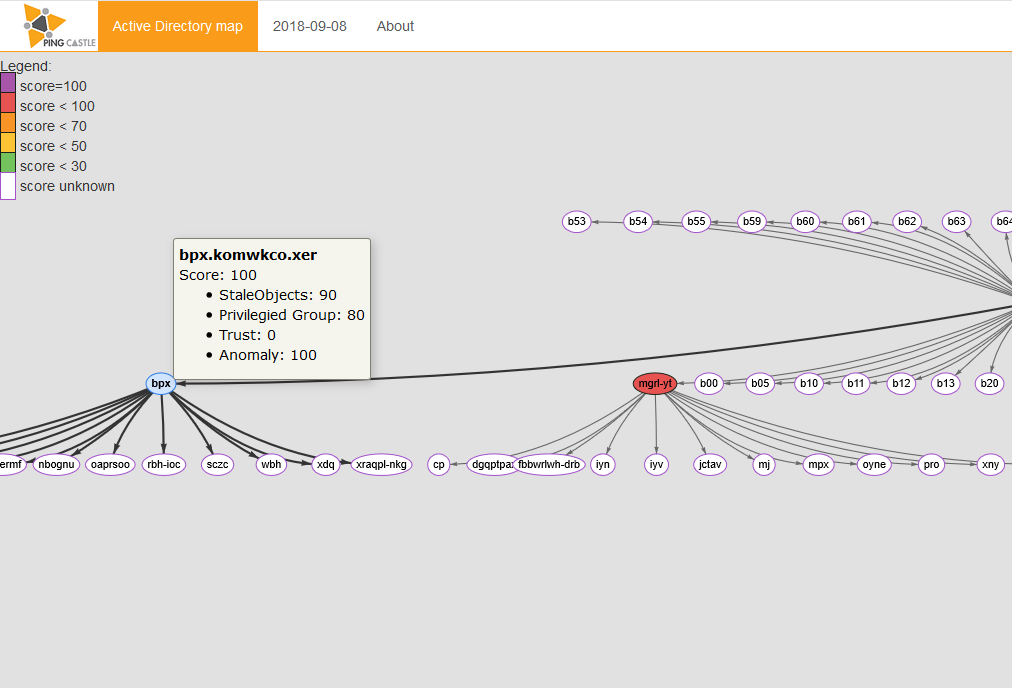
When available, the Active Directory health check score is displayed and colored by on it. Trusts are also colored based on the SID Filtering state.
Click on any image to open an example.
Internals
Algorithm to build the graph
PingCastle is using the data included in the report from the most reliable source to the less reliable source.
- The most reliable source is domain where the report has been generated.
- Then the tool is using direct trust data.
- Then the tool is using forest trust information. This information is located in the msDS-TrustForestTrustInfo attribute of a forest trust and in the partition element of the configuration binding context.
- The tool is using the information provided by the domain locator service when examining trusts. This information can add the Netbios name or the forest name of a trusted domain.
- If the “reachable” option has been set when producing a report, the tool is using domain SID found (in foreign security principals or sid history) to query the domain locator service and guess forest trusts.